SAML SSO
Requirements
- Your organization uses Google Workspace or Okta for authentication.
- You have an Admin role.
Roles
- Identity Provider (IdP): Google or Okta
- Service Provider: Auth0 (through Kubit)
JIT Provision
With SAML integration, once a user is created on your end (optionally included in a Security Group that has access to Kubit), that user can log in to Kubit immediately. The user profile information will also be automatically updated at every login time.
When a user is deleted/deactivated on your end, they will lose access to Kubit immediately too. There is no offline communication required.
Steps
SAML configuration is a process which consists of the following 6 steps. Kubit engineers will be available to support you with setting up and testing the integration.
1. Configure SAML app
Kubit will provide the exact configuration information required on your side. Below is just an example of general settings:
- App Name: Kubit
- Home page:
https://<YOUR_ORG>.kubit.ai - Logo:
https://<YOUR_ORG>.kubit.ai/images/Kubit.png - Single Sign On URL (also called ACS or Assertion Consumer Service URL):
https://kubit-<YOUR_ORG>.auth.<REGION>.amazoncognito.com/saml2/idpresponse - Audience URI (Entity ID):
urn:amazon:cognito:sp:<CONNECTION_ID>
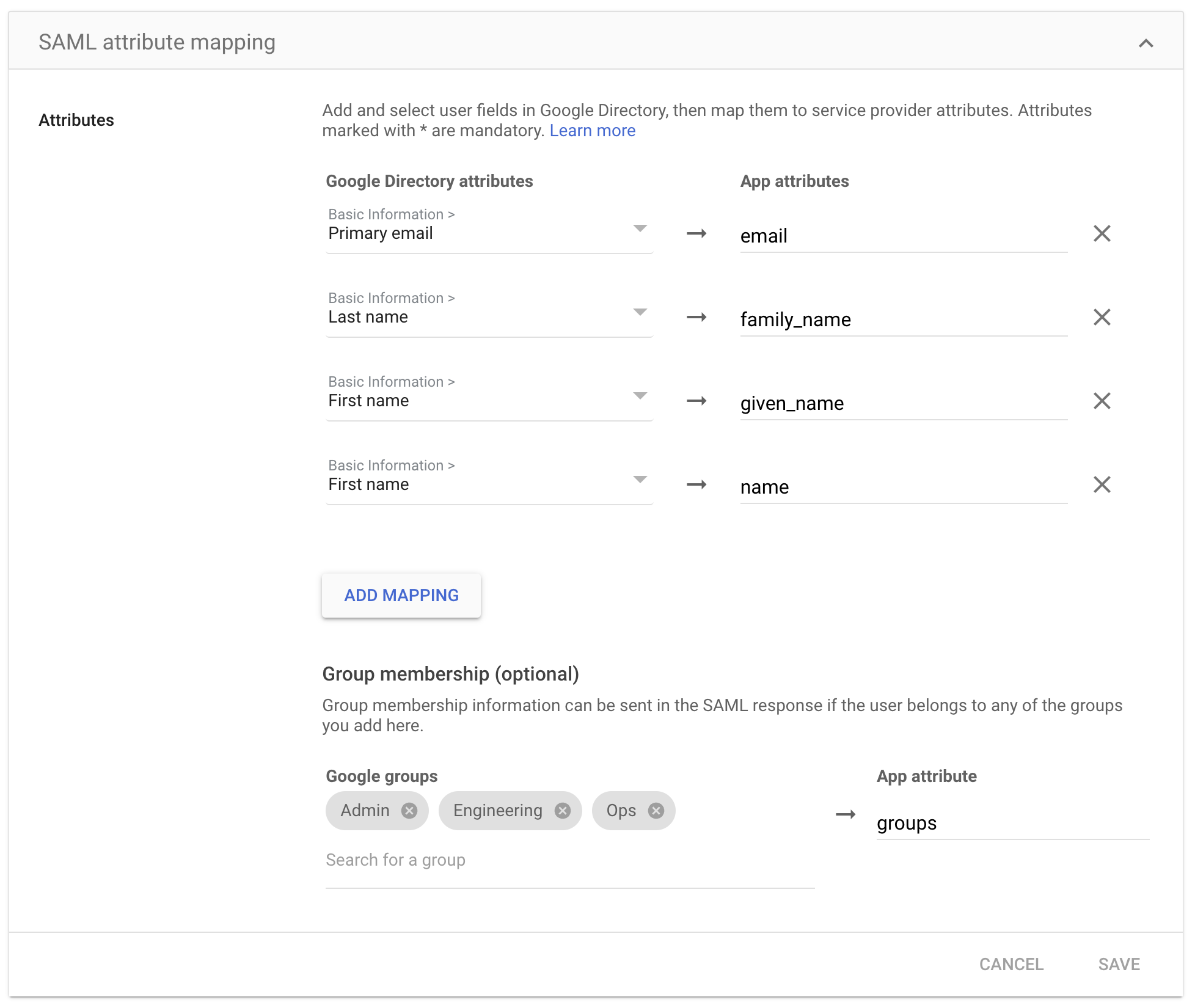
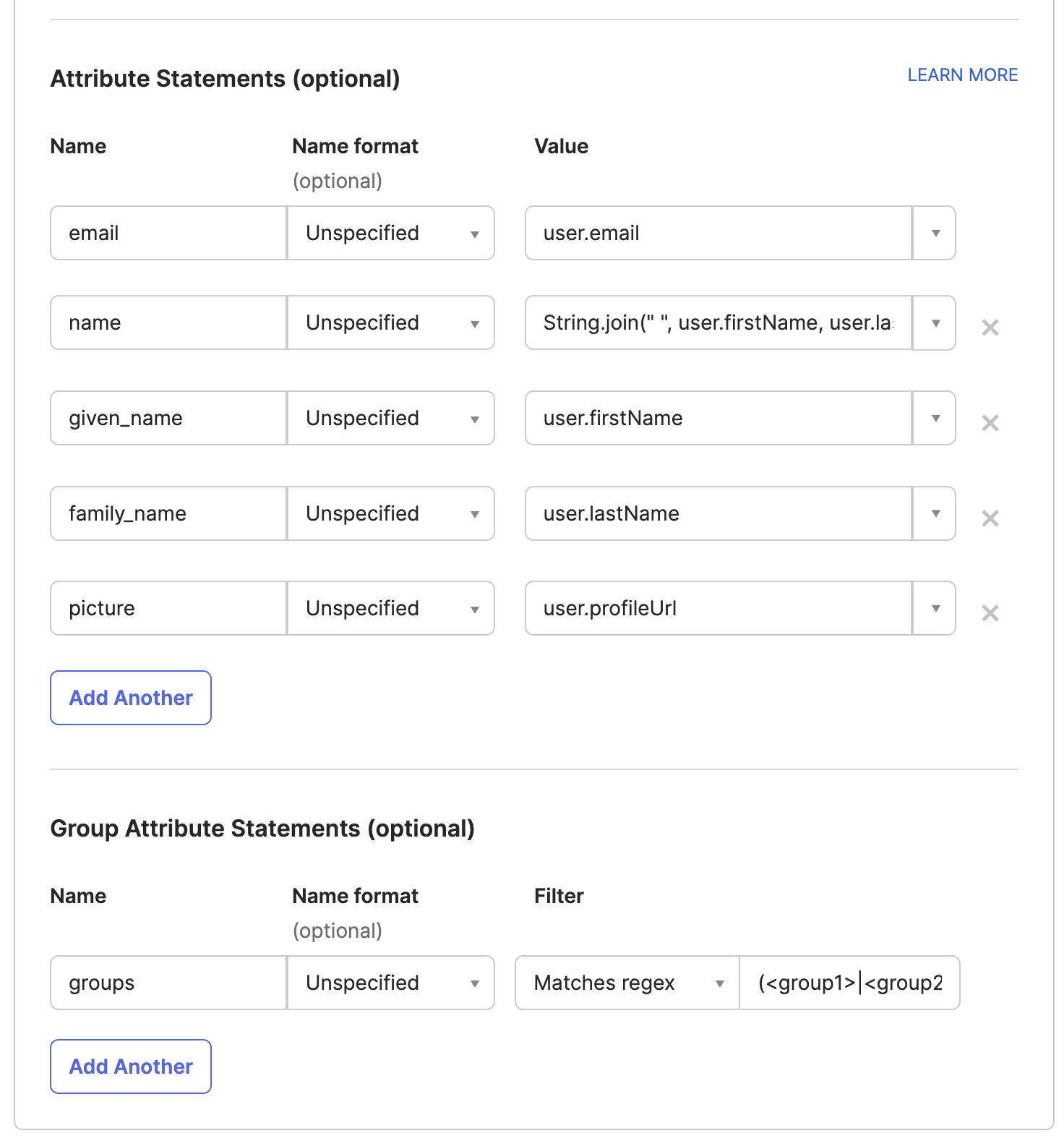
2. Map Attributes
Roles and PermissionsYou can manage permissions on the Kubit platform using your IdP groups by mapping the
groupsattribute. This step is mandatory for utilizing groups for permission management within the Kubit platform.
Google G-Suite
Okta
- Map
user.emailtoemail - Map
String.join(" ", user.firstName, user.lastName)to name #using Okta Expression Language - Map
user.firstNametogiven_name - Map
user.lastNametofamily_name - Map
user.profileUrltopicture
3. Respond
NoteOnce the SAML app is configured on your side, please provide the following information to Kubit support through a secure channel (e.g. Slack).
For Okta, a metadata file (sample URL https://*.okta.com/app/***/sso/saml/metadata) should include them all.
- Sign in URL (SSO URL / ACS URL) for your IdP.
- For Google, e.g.: https://accounts.google.com/o/saml2/idp?idpid=****
- For Okta, e.g.: https://**.okta.com/app/****/**/sso/saml
- X509 certificate in a .pem file
4. Test
Once configured properly on both sides, please work with Kubit support to test the integration. Make sure yourself has been assigned permission to access the Kubit app on your side. Try to access <https://<YOUR_ORG>.kubit.ai> Type in your organization's email. The password field will disappear with SSO enabled. Click on Sign In
5. Open Access
Google
You may choose to turn on Kubit App to everyone, or a specific group
Okta
Assign Kubit App to specific users
6. Idp-Initiated SSO
Due to security concerns, Kubit doesn't support Idp-Initiated SSO. The user has to go to the Kubit website first to initiate the login (SP-Initiated).
Google
Clicking on the Kubit App logo on Google Workspace Dashboard would fail. We don't know a way to hide that logo.
Okta
Caution!Please, hide the Kubit SSO App from users and create a Bookmark App instead. Attempted logins to Kubit from the SSO App will fail unless it is a Bookmark App.
References
Updated about 1 month ago